Screen Locks Are a Form of Endpoint Device Security Control
Put Time Back In Your Day Get Peace of Mind with Sophisticated Endpoint Protection. In a Bring Your Own Device BYOD policy the user acceptance component may include separation of private data from business data.
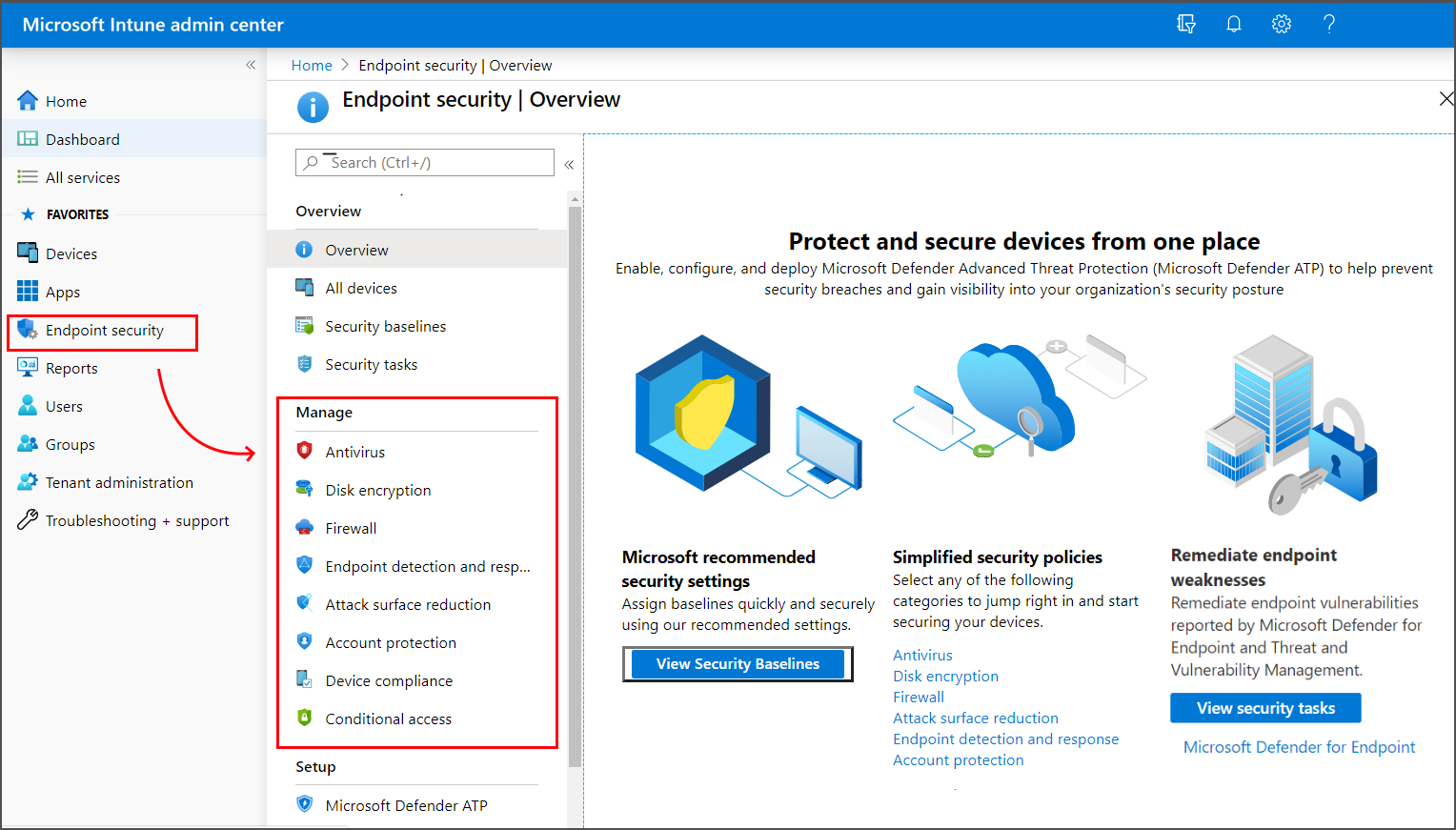
Manage Endpoint Security In Microsoft Intune Microsoft Docs
A key lock or an equivalent control eg.
. Microsoft Defender for Endpoint has an integration with Azure Information Protection AIP that shares sensitive data user activity and device risk data. The most common endpoint protection is a. Screen lock is a security feature for computers and mobile devices that helps prevent unauthorized access to the device.
Sign in to vote. The Government Information Security Reform Act Security Reform Act of 2000 focuses on. I use this link on open.
Why Endpoint Security Extends Beyond Antivirus. Endpoint device control is critical to protecting organizations. Thus data loss prevention is one of the.
An endpoint is any device that provides an entry point to. In summary organizations are facing many issues with endpoint device security risks as new forms of cyber-attacks continue to develop and evolve. Endpoints serve as points of access to an enterprise network and create.
Skip to main content. Put Time Back In Your Day Get Peace of Mind with Sophisticated Endpoint Protection. Password access when not in use.
Endpoint security provides an end-to-end data encryption feature that secures the companys data and keeps it safe from cybercriminals. Answer to Solved Screen locks are a form of endpoint device security. Remote wiping is a device security control that allows an organization to remotely erase data.
How to control USB devices and other removable media using Microsoft Defender for Endpoint. Ad Reduce The Risk of Breaches and Endpoint Attacks. Screen after 2 minutes of inactivity.
Did you try the Device Configuration profile for Windows 10 and later. Also known as a screenlock or lock screen a. Device Control is the branch of endpoint security that refers to the control of devices access to computers.
A string identified the device in the system for example. Endpoint security refers to securing endpoints or end-user devices like desktops laptops and mobile devices. Screen locks are a form of endpoint device security control.
Hi all I cant seem to get the screen lock or desktop image to work through intune I use a URL which is the location of the image which I save in sharepoint. True Screen locks are a form of endpoint device. Endpoint Detection and Response EDR helps find threats that slip past AV or NGAV.
Due to these new. An alteration threat violates information integrity. Screen locks are a form of endpoint device security control.
The Device Control technology allows network administrators to improve productivity by enforcing policies deny access force read-only access etc on multiple device types USB. Endpoint protection Local device security options Interactive Logon Minutes of lock. Endpoint and Device Security.
An EPP solution is a preventative tool that performs point-in-time protection by inspecting and scanning files once they enter a network. Ad Reduce The Risk of Breaches and Endpoint Attacks. When monitored via an AI-driven security operations and analytics platform EDR may.
Endpoint security is the practice of protecting enterprise networks against threats originating from on-premises or remote devices. Spending on endpoint security is also increasing with 24 of IT budgets on average going to secure endpoint devices. This article describes the settings in the device configuration Endpoint protection template.
HIPAA 164312a The device automatically locks. Microsoft Intune includes many settings to help protect your devices.

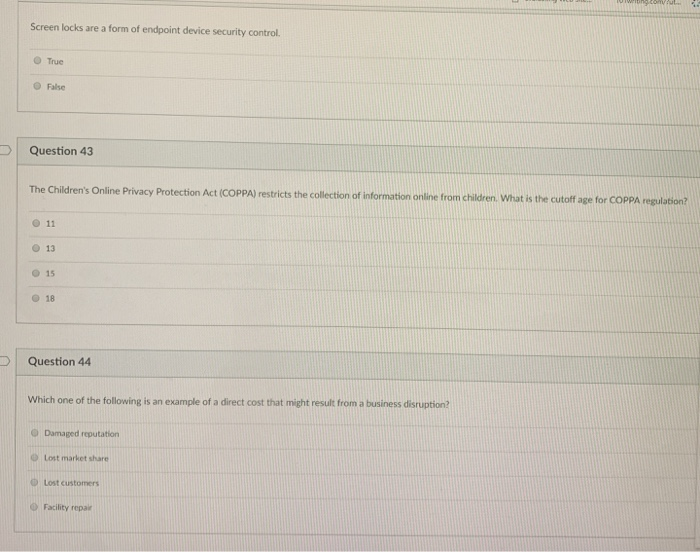
Solved Screen Locks Are A Form Of Endpoint Device Security Chegg Com

Manage Devices With Endpoint Security In Microsoft Intune Microsoft Docs
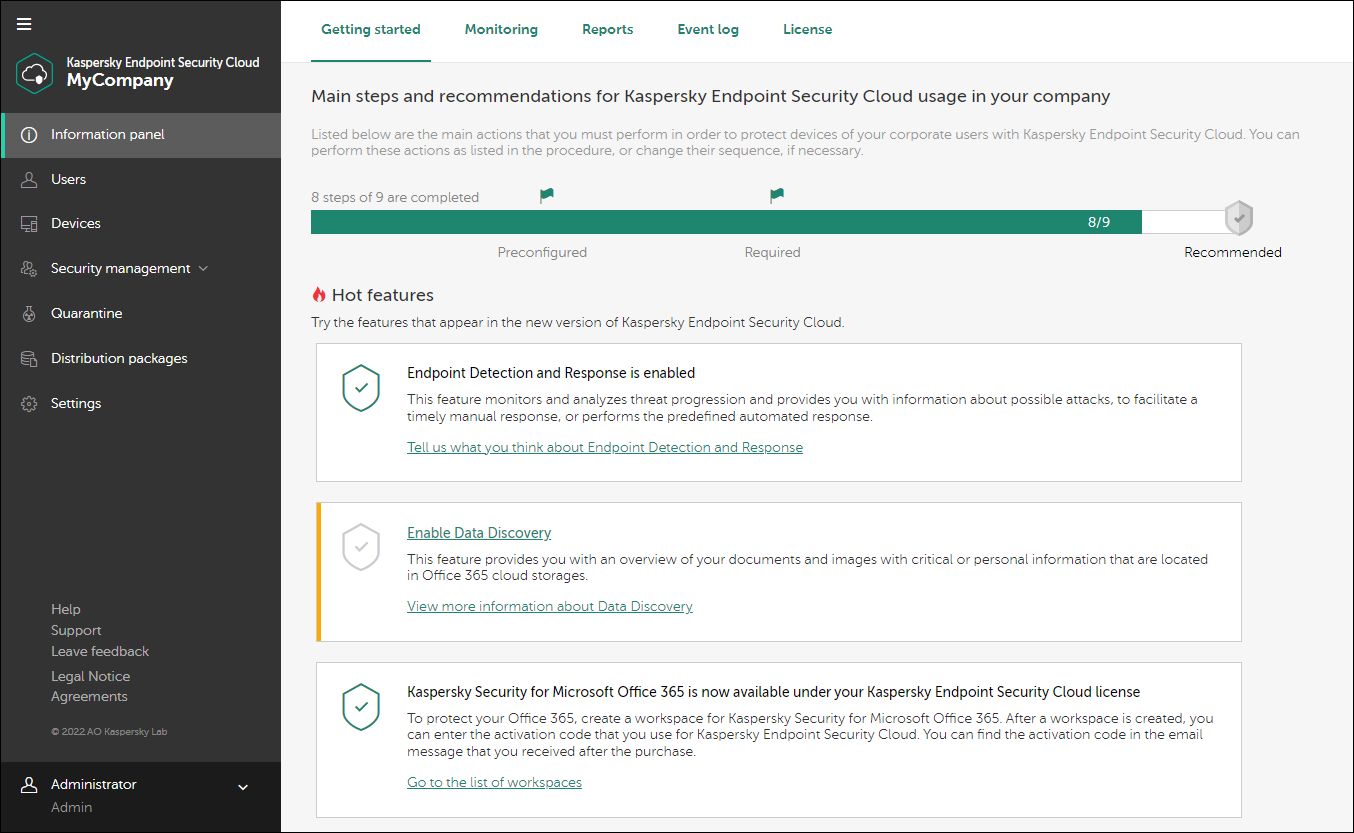
Interface Of Kaspersky Endpoint Security Cloud Management Console

Comments
Post a Comment